Secure Your Database At The Application Level
Atakama’s database encryption solution protects sensitive information both when it is stored at rest on the server and when the data is being transmitted to the application being used to access the data. Unlike other solutions, such as Transparent Database Encryption (TDE) that acquire complete, table-wide access the instant a user enters their credentials, Atakama keeps sensitive and non-public data encrypted until the user requests specific access.
With Atakama’s Application Level Encryption (ALE), the only time data is accessible is when Atakama’s API—depending on your application’s architecture, Atakama’s ALE can also operate as a transparent ODBC or REST proxy running on the user’s endpoint, which can be beneficial for legacy applications or systems where access to source code is unavailable—is used to decrypt the data within the application itself. The data is only decrypted for the particular user within their browser and remains encrypted on the server at all times.
Request a Demo for Atakama's Encryption For Your Database Today
The Encrypted Database User Experience
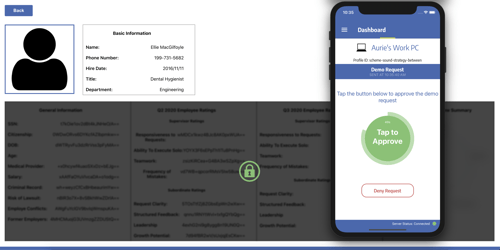
How Atakama's Encrypted Database Works
- Data is encrypted within the application as it is entered—before it is transmitted to the database
- Data is decrypted within the application when the data request is approved by the user
- User navigates to the database record—non-sensitive public information is viewable but any non-public, private, sensitive, etc., information remains encrypted
- When the user clicks to decrypt the record within the legacy application, the Atakama agent running on the user’s workstation or in the user’s browser, sends a notification to the user’s smartphone
- The user receives the authorization request on their associated Atakama Mobile app running on their smartphone
- By tapping approve, the smartphone sends to the workstation the piece of the decryption key for the specific record that is being decrypted
- The piece of the decryption key from the smartphone is reconstituted with the piece of the decryption key residing on the workstation and the record is decrypted and displayed.
Seamless Interaction with Data at the Application Level
Files protected by Atakama have their keys split into smaller pieces that are each stored on a different device. Atakama begins the process of opening the file by requesting the correct key fragments from the user's devices.

After the user approves with a tap on their mobile device, the piece of the file's unique key stored on that device is securely transmitted back to the requesting computer for Atakama to reconstruct.

Atakama confirms that the necessary pieces of the key have been correctly rebuilt before decrypting and opening the file. This entire decryption and file opening process takes place instantly within the OS-native interface.