Share Encrypted Files Externally With Confidence
Emailing files to third parties is an essential need for every business. But when sensitive files are sent outside the organization, the classified information is at risk. To minimize the risk, businesses turn to encryption. In practice however, sending encrypted files to third parties is a pain and is not necessarily the most secure way to mitigate the risk. With a user friendly workflow that ensures the intended recipient is the only person who will receive the files that are being shared with them, Atakama enables the secure transfer of files to external parties.

Try Encrypted File Transfer For Your Business, For Free
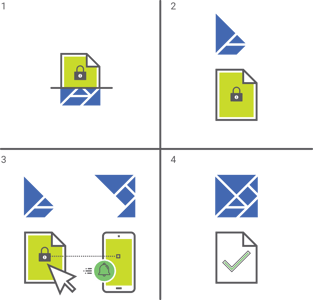
How Atakama's Encrypted File Transfer Works
Users can send encrypted files to recipients in a few simple steps:
- Right click on the encrypted file(s) to auto-generate a secure URL.
- Send the URL to the intended recipient by email or any other communication method.
- The recipient opens the URL in a browser.
- The sender is notified that the recipient is ready to download the file.
- The sender uses the Atakama Mobile app to approve the release of the file, which the recipient can now download in their browser.
The User Experience
Seamless Military-Grade Security For Files:
Files protected by Atakama have their keys split into smaller pieces that are each stored on a different device. Atakama begins the process of opening the file by requesting the correct key fragments from the user's devices.

After the user approves with a tap on their mobile device, the piece of the file's unique key stored on that device is securely transmitted back to the requesting computer for Atakama to reconstruct.

Atakama confirms that the necessary pieces of the key have been correctly rebuilt before decrypting and opening the file. This entire decryption and file opening process takes place instantly within the OS-native interface.