Zero Trust File System: Drag and Drop to Secure Your Files
Atakama helps businesses employ Zero Trust security for files using advanced threshold cryptography that is location-based and does not rely on passwords. Simply drag and drop to encrypt files. You choose the location, which can be local, cloud, and network. The convenient user experience makes it easy and self-explanatory for your employees.

Try Atakama's Zero Trust File System For Your Business, For Free
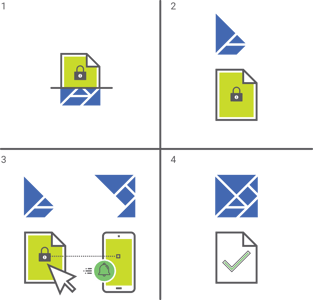
How Atakama Works
Distributed Key Management: Each file saved to the Atakama-enabled location is automatically encrypted using AES with a 256 bit key. The unique key for each file is then automatically fragmented into “key shards” and distributed to users’ physical devices.
The Zero Trust File System User Experience
Protecting Your Business's Files From Extortion Should Be Simple:
Files protected by Atakama have their keys split into smaller pieces that are each stored on a different device. Atakama begins the process of opening the file by requesting the correct key fragments from the user's devices.

After the user approves with a tap on their mobile device, the piece of the file's unique key stored on that device is securely transmitted back to the requesting computer for Atakama to reconstruct.

Atakama confirms that the necessary pieces of the key have been correctly rebuilt before decrypting and opening the file. This entire decryption and file opening process takes place instantly within the OS-native interface.